DDoS attacks can have a variety of impacts on businesses, websites, and e-commerce sites. Volume-based attacks saturate bandwidth by overwhelming networks. Because the attack traffic is so large, legitimate users are prevented from accessing the targeted resource. Such an attack may result in the blocking of legitimate bank transactions, eCommerce shoppers, and hospital patients from accessing their medical records. No matter the size of your business, the effects of a DDoS attack are significant.
What is DDoS Attack?
DoS (Distributed Denial of Service) is a type of cyberattack that hackers or cybercriminals use to make an online service, network resource, or host machine unavailable to its users on the Internet. During a DDoS attack, a machine and its supporting resources are flooded with thousands or even millions of requests that aren’t necessary. DDoS attacks are different from normal Denial of Service incidents because they come from a lot of different places or IP addresses. To get a sense of how big the DDoS threat is, the Check Point ThreatCloud Live Cyber Threat Map gives a global look at malware activity. It shows a map of DDoS attacks where exploits can be seen in real-time.
In botnet-related DDoS attacks, thousands of Internet-connected devices are taken over by hackers, who then direct all of those devices to send requests to the target at the same time. Attack tools that are both easy to obtain and easy to use have grown in popularity among hacktivists and organized crime groups over the past few years. DDoS assault apps like WebHive LOIC, which were originally designed for cybersecurity professionals to conduct “stresser” testing on websites, are now being used by criminals. They are not capable of launching a large-scale DDoS attack on their own. It is possible to take down large commercial websites for long periods of time when several stresser programs are coordinated together via a botnet or cloud service.
DDoS assaults might target a single component of the network connection or a combination of components. Layers of the OSI model are involved in every internet connection created. The three tiers of DDoS attacks are the most common:
- Network layer (Layer 3). Attacks that are on this layer include Smurf Attacks, ICMP Floods, and IP/ICMP Fragmentation.
- Transport layer (Layer 4). These attacks include SYN Floods, UDP Floods, and TCP Connection Exhaustion.
- Application layer (Layer 7). Mainly, HTTP-encrypted attacks.
Types of DDoS attacks
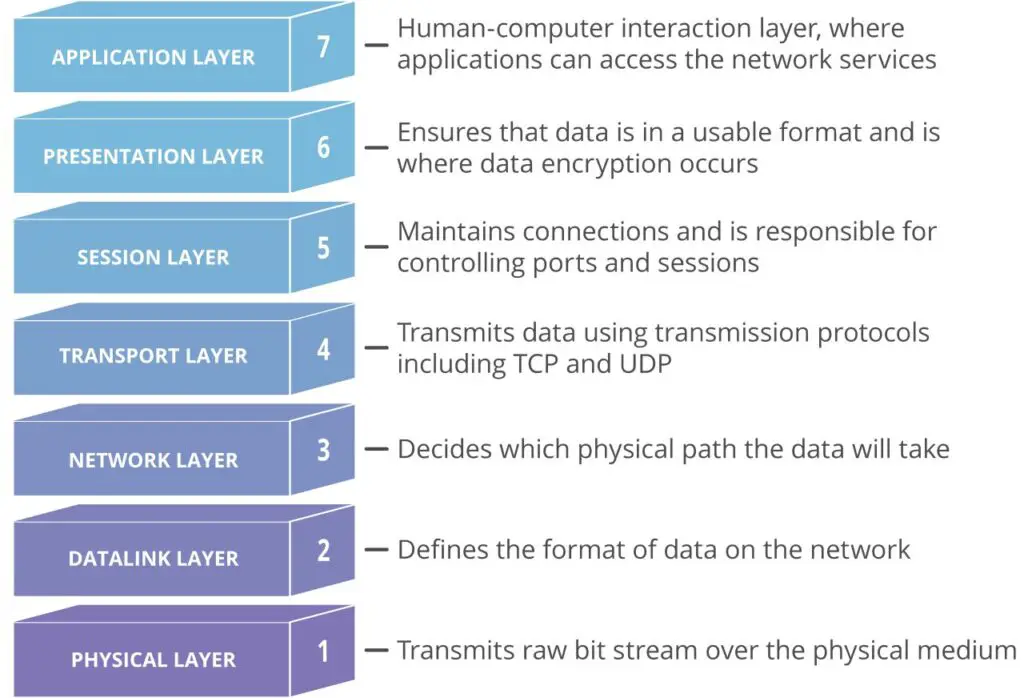
Depending on the sort of DDoS attack, different parts of a network are targeted. Understanding how a network connection is created is essential to understanding how DDoS assaults function.
On the Internet, a network connection is made up of a number of different “layers” or components. Each layer in the model has a distinct purpose, similar to the process of building a house from the ground up.
As depicted in the diagram below, the OSI model is used to represent network connectivity in seven separate layers.
1. Volume-based DDoS attacks
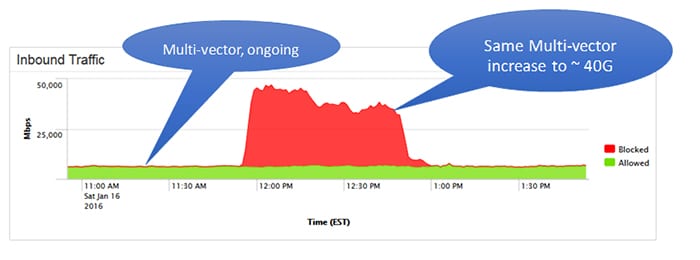
Volume-based DDoS attacks use massive amounts of inbound traffic to overload a target website. These attacks are commonplace and relatively easy to execute. These attacks typically use thousands or even tens of thousands of systems to flood a particular website with data. As such, they are often measured in bits per second and can cause significant disruption to the website. To counter volume-based DDoS attacks, you need to understand how such attacks work and how they can be prevented.
The most popular volume-based DDoS attacks include TCP-SYN floods and ICMP flooding. TCP-SYN floods bombard targeted websites with large amounts of malicious TCP SYN messages, causing resource exhaustion. According to Kaspersky, TCP-SYN is the most common DDoS attack in the fourth quarter of 2018. ICMP flood attacks overwhelm network bandwidth by sending ICMP echo-request packets in a massive quantity. This makes the targeted device inaccessible to normal traffic.
A similar type of attack uses a bot to send multiple data packets to overload a server or website. These attacks use weak spots in the infrastructure of the server or website and can crash the system. To counter volume-based DDoS attacks, you should protect your website from both types of attacks. In addition to limiting the amount of bandwidth, you should also take into account the amount of bandwidth that each of these methods consumes.
Another type of volume-based DDoS attack uses a spoofing IP address to overwhelm a targeted server. Another type uses ICMP floods to bombard network nodes with false error requests, rendering them unable to respond to real requests. Both of these attacks make use of compromised devices to send high volumes of traffic over a short period of time. In this way, volume-based DDoS attacks are extremely difficult to mitigate.
While software solutions provide partial protection from DDoS attacks, they cannot mitigate the effects of volume-based attacks. Locally installed software solutions are susceptible to large attacks, and a single device cannot keep up. Appliances provide scalability, whereas software solutions can become overwhelmed by a single large attack. This is because DDoS attacks use massive amounts of traffic to overwhelm a server with legitimate requests. Traditional firewalls are unable to effectively block these attacks and quickly become a bottleneck.
2. Burst attacks
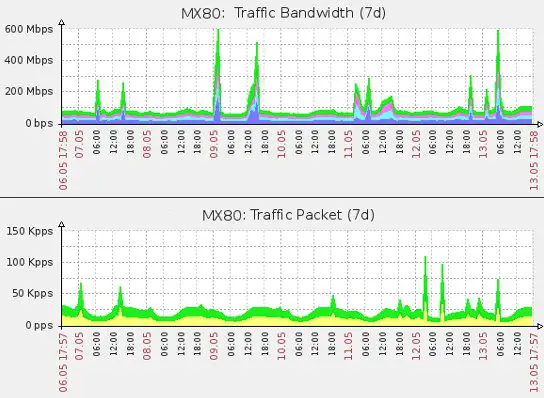
During the past year, DDoS “Burst attacks” have increased in number, duration, and complexity. One survey found that four out of five companies have been the target of DDoS attacks. These attacks have a short duration, with seventy to eighty percent of them lasting less than a minute. The attack vector changes from one burst to the next, so attack mitigation strategies must be adjusted in real-time across bursts.
Traditional on-premises DDoS protection solutions focus on in-line mitigation but fail to protect against pipe saturation. To combat this, a combination of on-premise and in-cloud DDoS protection solutions is the best choice. In this way, you can protect your organization from burst DDoS attacks while maintaining complete control over your network. And, unlike traditional solutions, combining cloud DDoS protection with on-premise mitigation is more cost-effective, accurate, and completely automated.
In order to counter these DDoS attacks, companies must implement a robust DDoS security strategy. Burst attacks are a common form of DDoS, and the best way to protect your business is to protect yourself from these attacks by learning about the risks and benefits of a secure network. DDoS attacks are more expensive than ever, but they can still cause major damage. If your company isn’t prepared, you’ll be left exposed to costly downtime.
One type of DDoS attack is called a “hit-and-run” attack. The attackers use high-volume application and network attacks to overwhelm a target service. They usually target gaming sites, but now they’re targeting all kinds of websites – from banks to shopping sites to websites promoting online gambling. These attacks can affect a company’s hosting service, preventing legitimate users from using it.
The June 21 DDOS attack was one of the largest in history, reaching its peak in less than two minutes. As a result, the volume of attacks increased by about five times over the year. Several new threat actors and hacktivist groups have emerged to take advantage of the increased level of vulnerability. No industry is immune to cyberattacks, so it’s imperative to protect your network from unauthorized users. The attacks that target an unprotected network can disrupt access to critical services and damage a company’s reputation.
3. Botnets
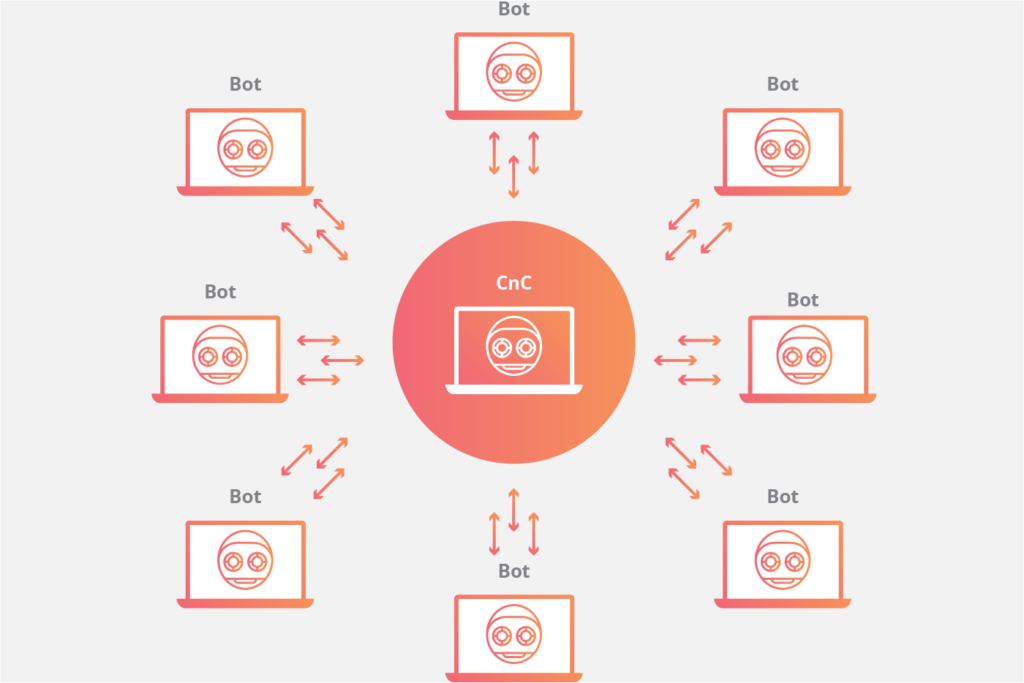
A DDoS attack is when a network of computers or ‘bots’ tries to overload one computer on the Internet, blocking legitimate requests from being made to the target. A DDoS attack can range from attacks on the victim’s server to sending spam disguised as human messages to e-mail accounts. While the latter may be annoying, they are not necessarily malicious. However, many botnets are designed to cause as much disruption as possible to their target’s system.
Botnets are used to attack websites and other online services, as well as to mine cryptocurrencies. More computers are becoming infected with mining software, and more digital wallets are being stolen from people’s computers. Botnets are also used to interfere in elections, steal personal information, or defraud advertisers. To combat the threat from botnets, it’s critical to learn more about this malicious use and how to protect yourself against it.
One way to prevent botnets from disrupting websites is to stop them from spreading. By disabling botnets, you will prevent them from ever harming a website again. If you want to prevent a DDoS attack, you must stop botnets before they cause any damage. Botnets are an essential part of the cybercrime landscape, so it is important to understand how they work.
DDoS attacks use botnets to carry out many different malicious tasks. A botnet is a group of internet-connected devices that are used by one or more perpetrators to attack a website. In a DDoS attack, a botnet can cause a server to be temporarily unavailable, making it inaccessible to legitimate customers. The resulting impact is that many sites will be unable to provide their services.
DDoS attacks can cause severe damage to the victims’ websites and are one of the biggest causes of network failures. Botnets can take over the internet by gaining control of infected computers. The hackers can also use these bots to collect data, install spyware on users’ computers, or monitor networks. Furthermore, they can be used as launching platforms for more malicious attacks. So, if you suspect that your company has been the victim of a botnet attack, you should take action right away.
4. Extortion
If you’re wondering whether or not Extortion is a DDoS attack, the answer is probably yes. This type of attack targets primarily security and privacy-conscious email providers, such as Mailfence and Runbox. Earlier attacks have targeted ZDNet and Bleeping Computer, and this latest campaign appears to be even more widespread. DDoS attacks are becoming more common than ever before, with some experts predicting that they will double by 2020.
When a DDoS extortion attack occurs, it targets a particular application or service. The attackers then overwhelm the target with attack traffic, resulting in service degradation and possibly even a crash. DDoS extortionists generally do not follow through on their threats, but they must be prepared for any eventuality. By enlisting the help of a DDoS mitigation provider, you’ll be better prepared to survive extortion attacks.
Another type of DDoS attack is cyber blackmail, in which the attacker tricked an employee into paying a ransom to decrypt a company’s files. The ransom is a cryptocurrency that the cybercriminal demands in exchange for restoring access. If the victim fails to pay the ransom, the cybercriminal will continue the attack until they’re paid or threatens to release unaired episodes of a popular TV show.
The number of ransom DDoS incidents has increased significantly since the beginning of 2020, as ransomware groups started using DDoS as an extortion technique. The Lazarus Bear Armada group impersonates state-sponsored groups, such as Fancy Bear (Russia), and the Lazarus Group in North Korea, to launch DDoS attacks. They claim to have 2 Tbps of DDoS capability and demand payment via Bitcoin or a cryptocurrency.
DDoS extortion attacks can be as subtle as personal emails sent to a customer. In some cases, attackers will send customized email messages to customers, as well as demand a ransom in exchange for a specific service. The most common form of DDoS extortion attack begins with an email-delivered malware that self-propagates throughout a network.
Types of DDoS Amplification
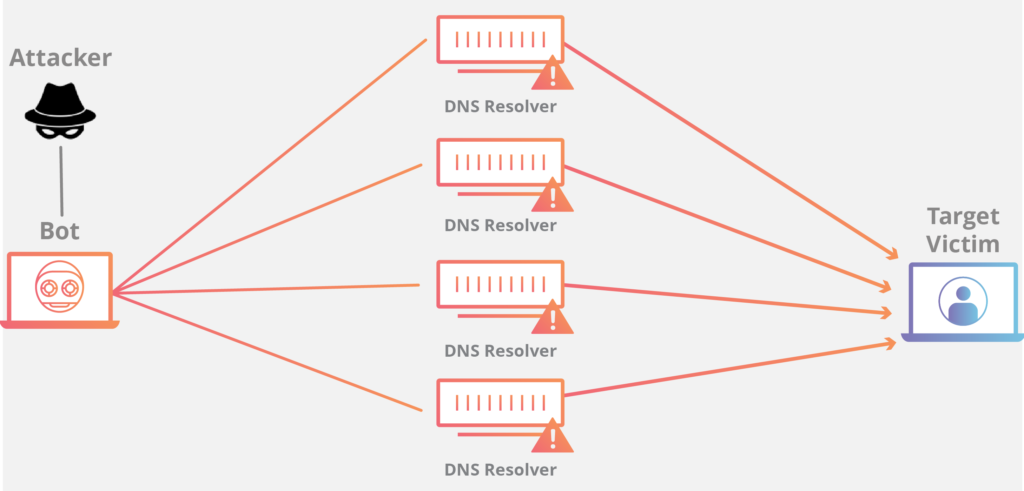
A DDoS amplification attack takes advantage of DNS server security flaws to amplify the impact of the initial DDoS attack. They amplify minor requests, reducing the bandwidth available to the victim and effectively terminating the functions of the unfortunate target server. DNS Reflection and CharGEN Reflection are two types of amplification attacks.
DNS reflection
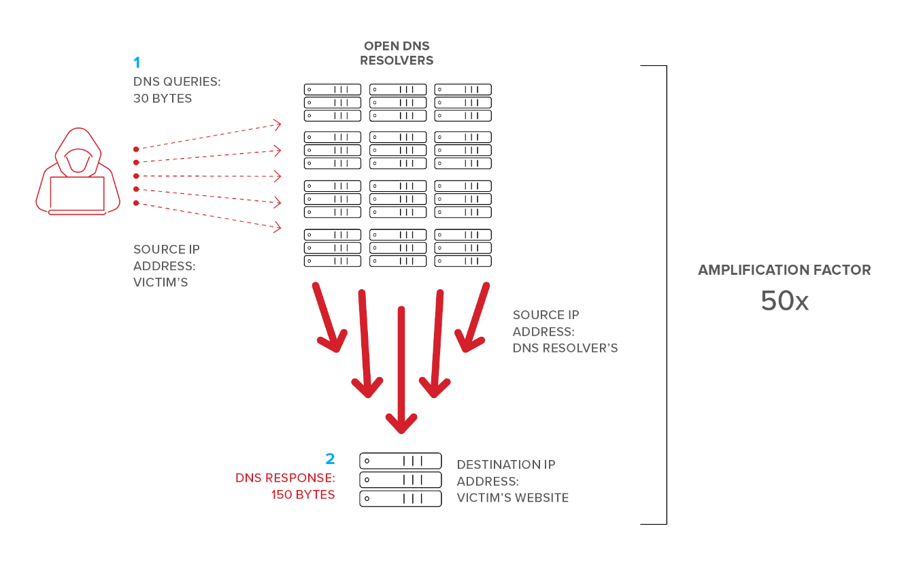
Searching for the IP address of a domain name you placed into your search box is the job of a DNS server. You might think of it as a phone book for the internet. One method of DNS reflection attacks is to send numerous requests to a DNS server in order to obtain the victim’s IP address. The responses have been observed to be 70 times larger than normal, resulting in an instantaneous overpowering of the sufferer.
CharGEN reflection
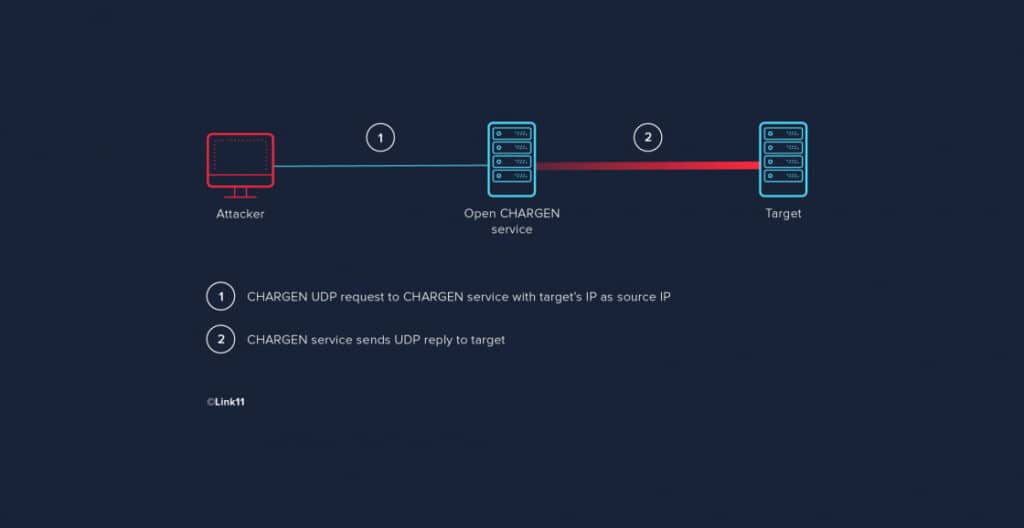
CharGEN, a debugging or testing protocol that was developed in 1983, is an outdated internet protocol by today’s standards. Unfortunately, this protocol is still actively used by many internet-connected printers or copy machines, allowing hackers to exploit CharGEN’s numerous age-induced flaws. The hacker will use the IP address of the victim to transmit a large number of little packets of data to whatever is running on CharGEN. In order to overwhelm the target server, the device sends a deluge of UDP (User Datagram Protocol) responses to the victim’s system.
DDoS attack numbers
Every year, as technology progresses and security systems get more advanced, so do the methods used to break into them. DDoS attacks have evolved tremendously since the 1990s, compared to attacks of that era.
In the 1990s, the average number of requests per second in a DDoS attack was just over 150. The 2018 GitHub attack, which was the largest reported successful DDoS attack in recent years, had a throughput of 1.35 terabits per second. While the site was temporarily down during the attack, it only did so for about eight minutes total.
How much does a DDoS attack cost?
In just 24 hours, a DDoS assault can cause significant financial harm to a company, which is reason enough to take proactive steps to prevent it from happening again in the future. It’s estimated that a single DDoS attack can cost as much as $50,000 in lost income, productivity losses, and the actual security costs of repelling it, according to a 2018 analysis from Corero Network Security. One has to wonder how much it costs to hire a cybercriminal and their bot army.
Prices for these services are hidden on the dark web, as they are with most illegal activities conducted over the internet. Based on the length of the DDoS attack, the cost of this service ranges from 300 seconds up to 10,800 seconds in duration (3 hours). Shorter attacks are obviously less expensive than longer ones.
Pseudo-subscription services are offered by many of the criminals that provide these services, which is odd. For 60 euros a month, for example, you can get 3 hours of access to one attack.
Is DDoSing illegal?
In several nations, DDoS attacks are illegal. The use of distributed denial-of-service attacks (DDoS) is punishable by fines and imprisonment in the United States, for example. While in most European nations, DDoSing can lead to an arrest, in the United Kingdom, you might be punished with up to ten years in prison.
Can you trace DDoS attacks?
Detecting a DDoS assault is challenging since it is disseminated over a large number of machines. The perpetrators of such attacks, on the other hand, frequently make an attempt to avoid detection.
When a DDoS assault occurs, specific cybersecurity tools can be used to analyze the traffic and identify it. However, it’s frequently too late to prevent them from happening. In best case scenario, you’ll be able to study the data and make future cybersecurity adjustments that are suitable.
Does a VPN help prevent DDoS?
Most commonly, DDoSing is done to threaten or hurt a company’s reputation or sales by threatening or harming a company’s developers or publishers. Individual users, on the other hand, maybe impacted. Online players are more prone to this. In the case of competitive gaming, your opponent may attempt to disrupt your gameplay via DDoS, which is not a security problem per se but can be quite frustrating.
There is nothing you can do to prevent the game server from being hacked. P2P games, on the other hand, allow opponents to find your IP address and use it to disrupt your gameplay. Using a VPN to hide your real IP address will help you avoid this. DoS attacks are impossible if malicious actors are unaware of your genuine IP address.
How to Prevent DDoS Attacks?
- When dealing with DDoS attacks, it’s best to use a hybrid solution that combines both on-premises and cloud-based resources.
- Extend your security perimeters with many layers of defense to thwart DDoS attacks on your network.
- Develop an incident response team capable of deploying additional resources in the case of a DDoS assault.
Key Takeaways
As part of an efficient cyber security strategy, it’s essential to have an infrastructure that can detect, prevent, and respond to DDoS attacks. An ever-changing danger is distributed denial-of-service (DDoS) assaults. Large-scale service disruptions affecting well-known brands and well-known financial institutions continue to garner the most press attention. Despite this, lower-intensity DDoS assaults are frequently used by hackers to target government, education, travel and hospitality, technology, utilities, and other sectors.








